Architecture
Shieldoo’s network architecture is built upon an open-source piece of technology called Nebula (by Slack).
To learn how Nebula works, use the following resources:
- Nebula
Official Nebula documentation explaining the core concepts and features in technical detail. - What Is Nebula and How Does Work?
A blog post done by Shieldoo explains Nebula’s value, such as its speed, simplicity and security.
The Shieldoo web application allows you to interact with the network architecture using the following features:
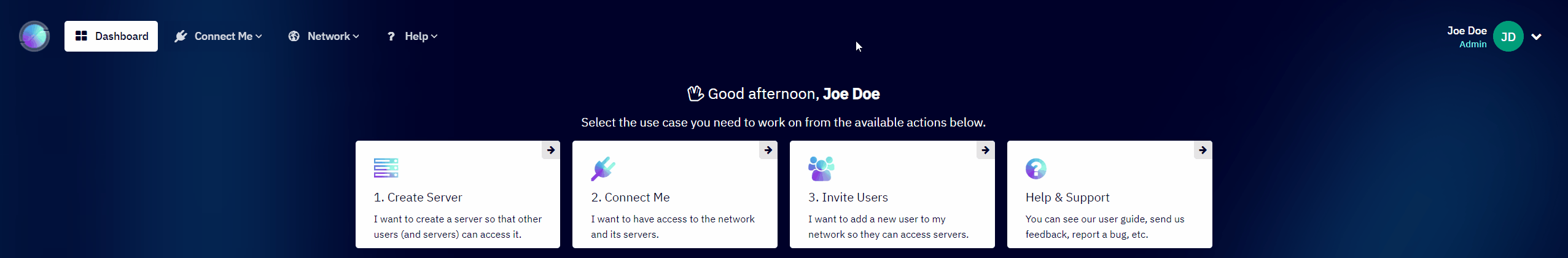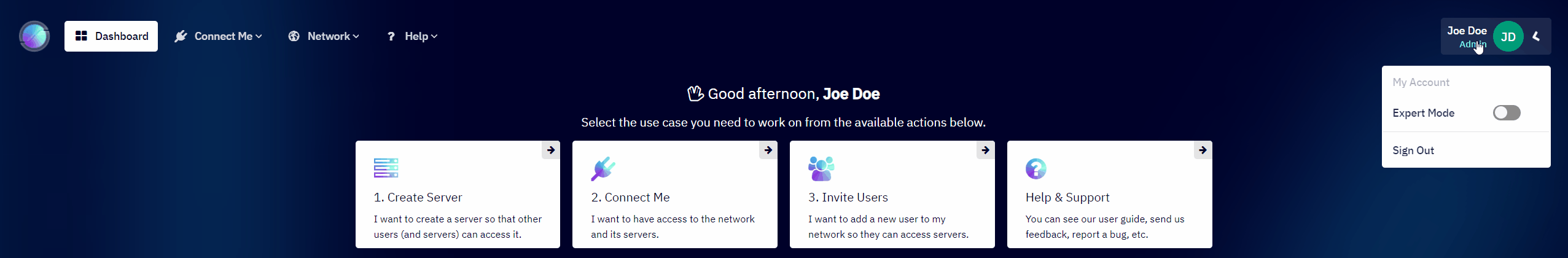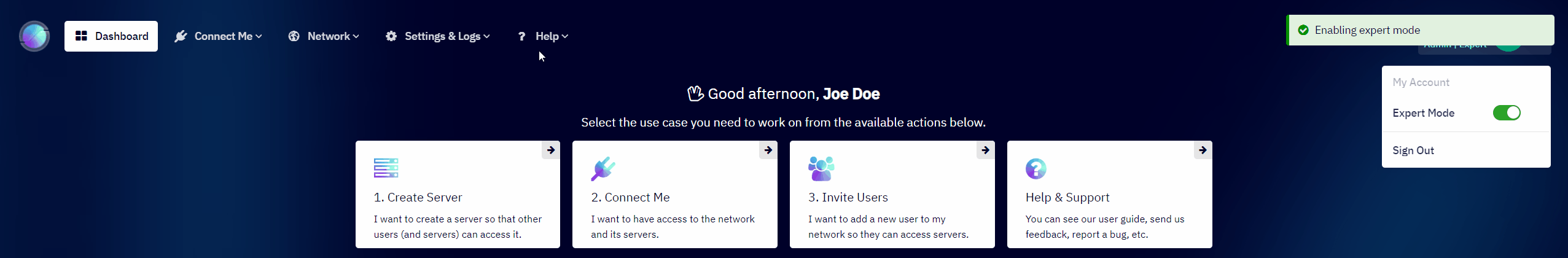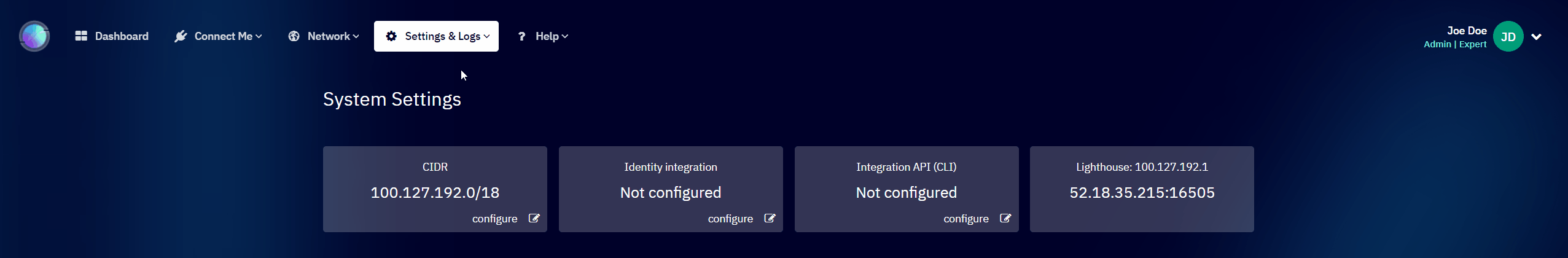
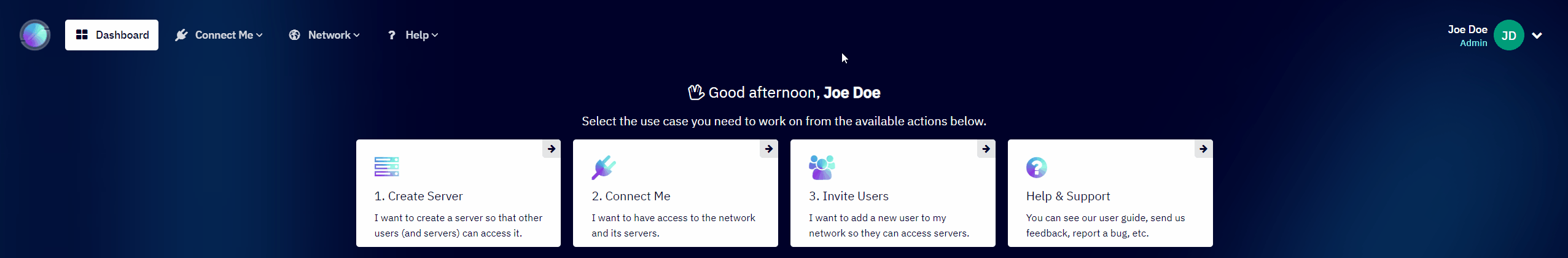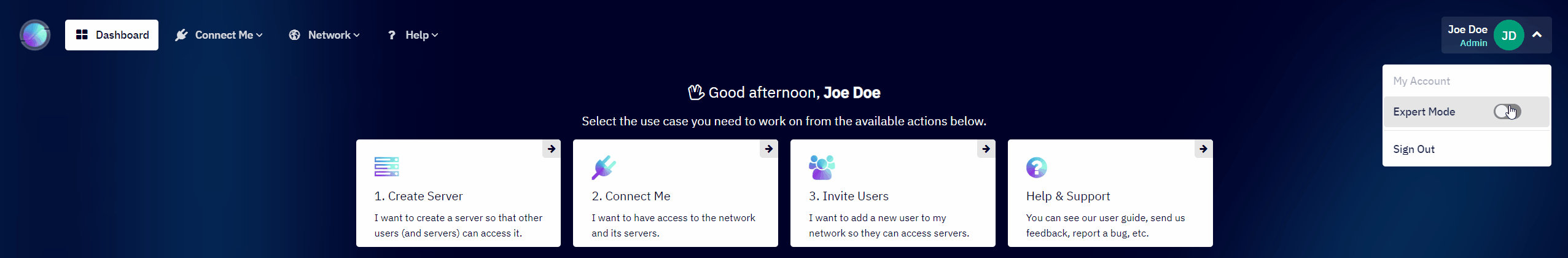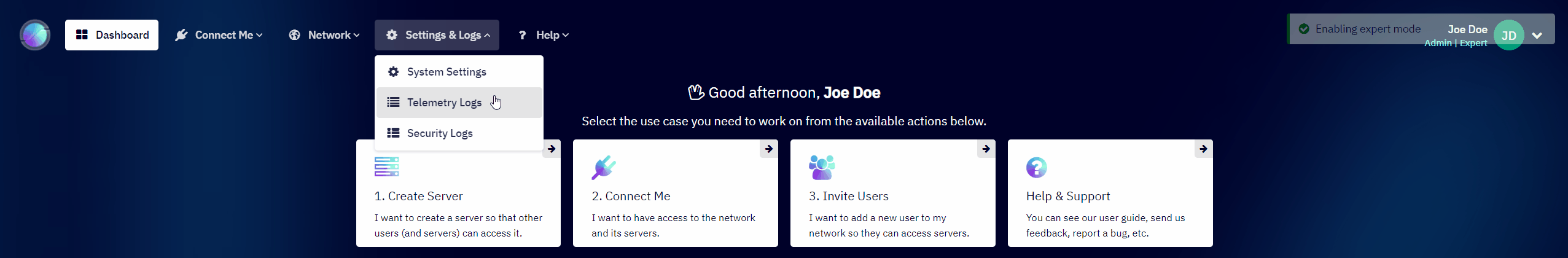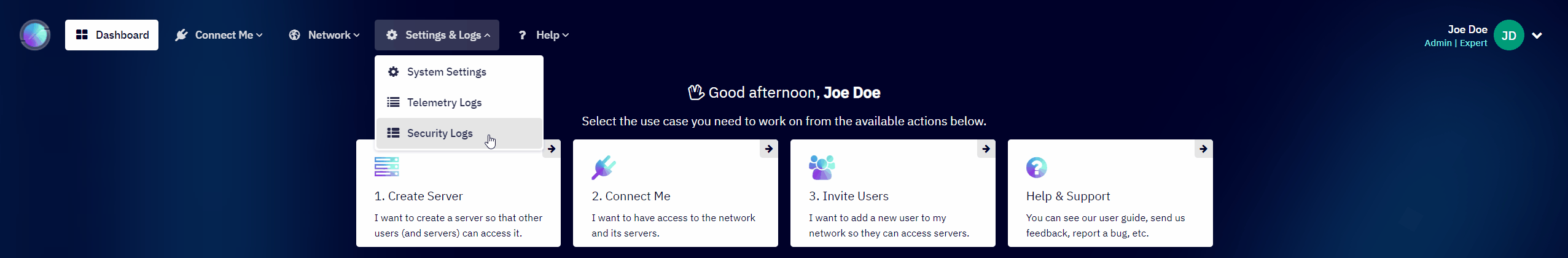
System Settings
System Settings allows you to configure the network architecture of your Shieldoo Secure Network.
- Log in to your organization’s Shieldoo Secure Network web application.
- Enable Expert Mode
- See the Access Management chapter to learn how to enable Expert Mode.
- Go to the Settings & Logs | System Settings section.
- It allows you to do the following:
- Configure the CIDR of your Shieldoo Secure Network.
- Configure the Identity Integration.
- Configure the API Integration (CLI).
- See the list of Lighthouses that exist in your Shieldoo Secure Network.
- See the list of Cost Usage.
Changing the CIDR of your Shieldoo Secure Network causes all access certificates and IP addresses of nodes (servers and clients) to be regenerated. Only do this if you fully understand the implications.
Lighthouses
In a Nebula network, a lighthouse is an essential component. It is a public host that helps network nodes (users and servers) discover routes to one another.
A lighthouse tracks network nodes, directing their traffic. When two nodes want to communicate with each other, a lighthouse finds the fastest route for them, allowing them to communicate directly. There is no central server creating traffic bottlenecks as with traditional VPN solutions.
Shieldoo Secure Network automatically deploys lighthouses for you.
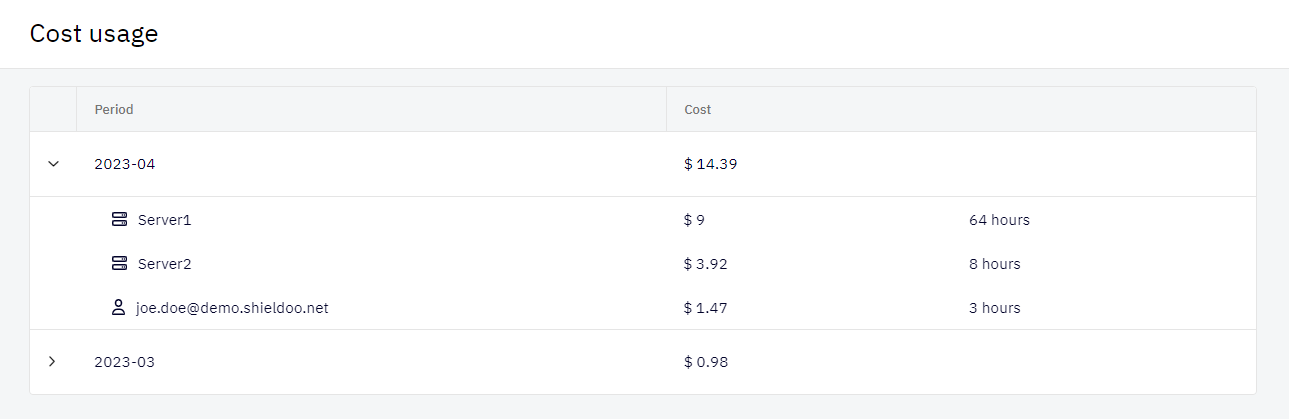
Cost usage
Here you can see the cost usage by month and by specific users and servers.
For more price information, please visit the pricing section of our website.
Telemetry and Security Logs
Telemetry and Security Logs can provide a wealth of information to help you monitor, troubleshoot, and secure your Shieldoo Secure Network.
- Log in to your organization’s Shieldoo Secure Network web application.
- Enable Expert Mode
- See the Access Management chapter to learn how to enable Expert Mode.
- Go to the Settings & Logs | Telemetry Logs or Security Logs section.
Shieldoo Secure Network keeps telemetry and security logs for nine days as standard.