Identity Integration
Shieldoo Secure Network supports Microsoft Azure AD (Active Directory) integration, which brings enhanced security and simplified management to your IT infrastructure. By leveraging Azure AD, you can seamlessly manage users and groups within Shieldoo, ensuring a secure and organized environment for your servers and firewalls.
Configuration Identity integration
Azure AD Application
Shieldoo Secure Network and Azure AD are integrated via an AD application known as a service principal. This application is responsible for reading groups and users from your Azure AD, making it easy to manage Shieldoo Secure Network groups and users without duplicating efforts.
Configuration Azure AD Application
- Log in to the Azure portal.
- Go to the Azure AD | App registrations section.
- Register a new application.
- Configure the following settings:
- Add a new client secret in the Certificates & Secrets section (we recommend saving the secret value).
- Add Application permission and Grant admin consent for your organization:
- Microsoft Graph: User.Read.All
- Microsoft Graph: Group.Read.All
- Microsoft Graph: GroupMember.Read.All
Azure AD Group
Next, create a group within Azure AD containing users with admin rights in Shieldoo Secure Network (Shieldoo admins). These admins can manage Shieldoo Secure Network settings and configurations. Centralizing the management admin in one Azure AD group allows you to easily add or remove users as needed, streamlining your security administration process.
Configuration Azure AD Group
- Log in to the Azure portal.
- Go to the Azure AD | Groups section.
- Create a new group.
- To the group, add admins in Shieldoo Secure Network.
Don’t forget to group Shieldoo admin, including yourself (who configured the Identity integration), as you could lose access to the Shieldoo Secure Network web application.
Shieldoo Secure Network
In the last step, set up Identity integration in Shieldoo Secure Network.
Configuration Identity integration
- Log in to your organization’s Shieldoo Secure Network web application.
- Enable Expert Mode
- See the Access Management chapter to learn how to enable Expert Mode.
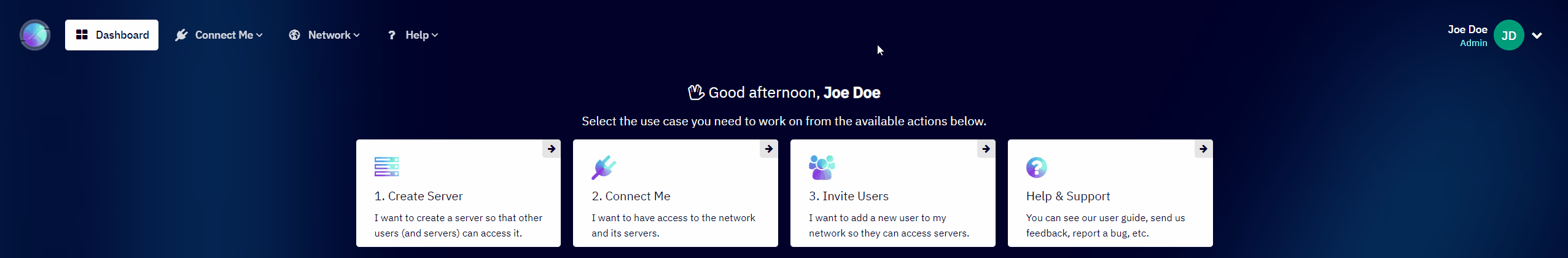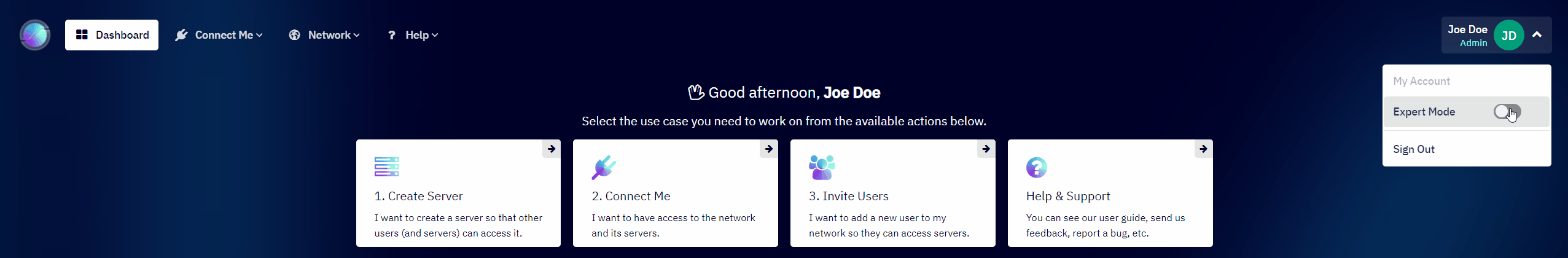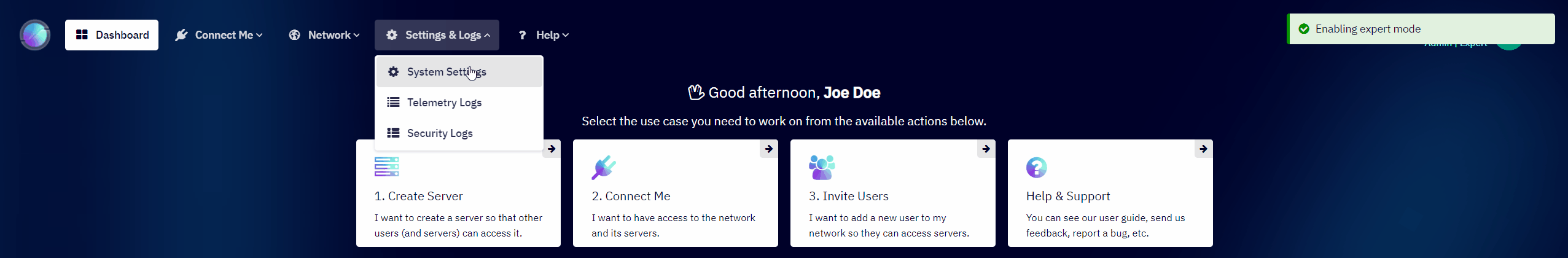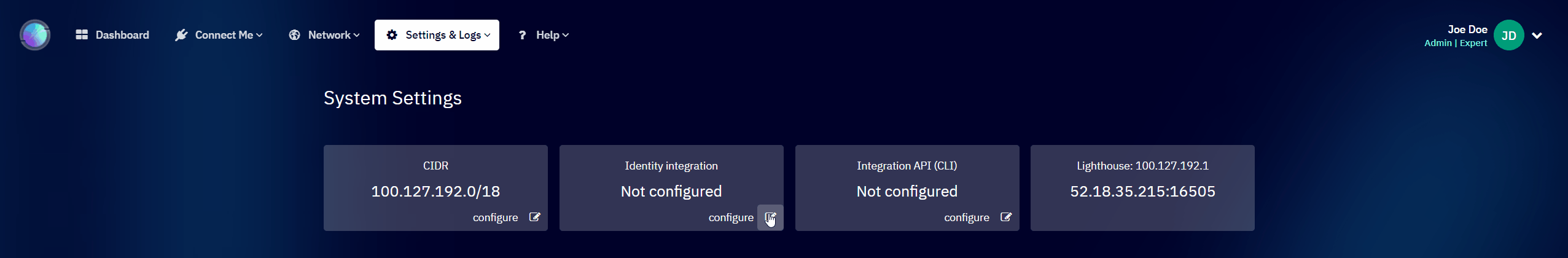
- Go to the Settings & Logs | System Settings section.
- In the Identity integration section, click the configure button to open the settings dialog.
- Configuration of the Identity integration settings:
- Tenant Id
- Client Id
- Client secret
- Shieldoo admin group ObjectId
- Click on the Save button to confirm setting Identity integration.
Use Identity integration
When creating server and firewall configurations in Shieldoo Secure Network, Azure AD Groups are utilized for defining rules and importing members. This ensures that your organization’s access controls are consistently applied across all servers and firewalls, improving overall security. In addition, groups are replicated from Azure AD into Shieldoo Secure Network when Identity integration is successfully configured, and you can start using them immediately.
Users are replicated from Azure AD into Shieldoo Secure Network in two ways:
- Admin - When Identity integration is successfully configured, admins (users of group Shieldoo Admin) are replicated from the Azure AD group into Shieldoo Secure Network, and you can start using them immediately.
- Users - Other users are replicated ad-hoc from Azure AD groups based on using a specific group in the inbound firewall rules.
See the Access Management chapter to learn how to set up access rights and firewall configuration.
By default, when you set up your Shieldoo Secure Network, all network nodes (users and servers) can access each other. We highly recommend that you secure the user nodes in your network a specific firewall. Learn how to do that in the Securing Users section.
By default, a user replicated with specific settings from the default Access Card Template in Shieldoo Secure Network. This ensures that your security policies are consistently applied across your entire organization.
If you want to use a different setting, we recommend that you change the setting in the default Access Card Template as follows:
- Log in to your organization’s Shieldoo Secure Network web application.
- Enable Expert Mode
- See the Access Management chapter to learn how to enable Expert Mode.
- Go to the Network | Access Card Templates section.
- Open the context menu of the default Access Card Template and select the Edit button to change specific settings:
- Firewall configuration
- Groups
- Valid till
- Description
Check out the Access Management chapter if you need more information about the Access Card Template.
Replicating groups and users from Azure AD into Shieldoo Secure Network can be done in two ways:
- Automatic replication takes place every 20 minutes.
- Manual replication takes 1 minute.
- Go to the Settings & Logs | System Settings section.
- In the Identity integration section, click the configure button to open the settings dialog.
- Click on the Save button to confirm setting Identity integration.
Identity integration setting changes some features
After successfully configuring the Identity integration, some features will change in the Shieldoo web application:
- The create group feature is enabled because it is required to create server-to-server access within the Shieldoo Secure Network. For more information about this feature, see in Access Management chapter.
- The invite user feature is disabled because users are replicated from the Azure AD. For more information about this feature, see in Users chapter.
- The edit and grant/revoke admin rights are disabled for the user because these functions are controlled in Azure AD. For more information about this feature, see in Users chapter.
- The create multiple Access Cards feature is disabled for a user because Identity integration controls access based on groups. For more information about this feature, see in Access Management chapter in Creating User Access Cards section.